Using AWS Organizations and AWS Nuke to create disposable low-cost cloud experience
Every beginner in AWS

Most AWS users in beginning miss to keep track of services they create. It’s very easy to forget the services creating via console in different regions. AWS is definitely a sea of services.
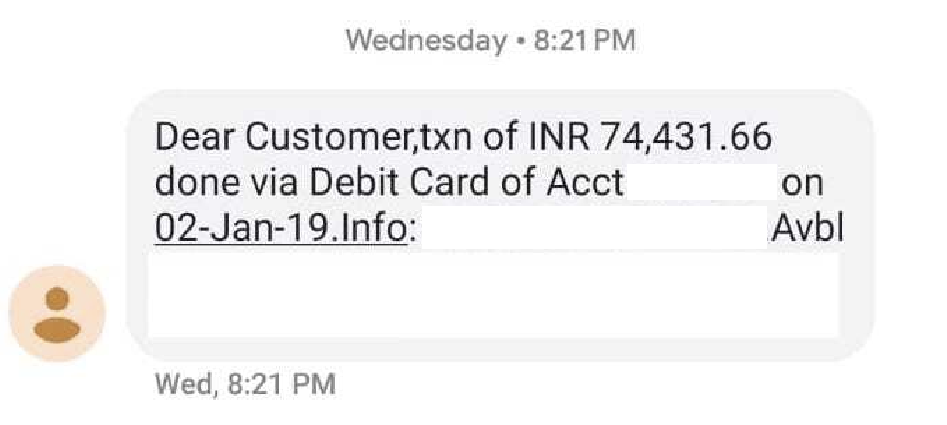
I myself have lost over 5000 in three occasions in total. With one alone being 4,000$ because I left a P5d.large Nvidia H100 GPU running which I created for an experiment.
Using AWS billings and alarms are some of the easiest way to keep track of AWS expenses. I also encourage using AWS organizations for centralised billing to utilise AWS accounts as disposals resources for all experiments and testing purposes.
I’ve written other blogs on using AWS billing and alarms and using AWS organizations effectively. In this article we will explore using AWS Nuke a powerful tool for destroying AWS resources.
I’m writing this blog as step by step lab instruction so that you can easily follow it just by running the given commands in sequence.
Objective of the lab:
Understand the purpose and functionalities of AWS Nuke.
Set up AWS Nuke for safe experimentation.
Write configurations to target specific resources for deletion.
Execute a dry run to simulate resource deletion.
Prerequisites
To finish this lab you should have:
An AWS account with access credentials. Preferably with some resources created.
Basic understanding of AWS resources.
Familiarity with the command line interface (CLI).
Use cases:
Destroying the disposable AWS accounts created for testing and experiments.
Destroying inter-dependable AWS resources which are otherwise hard to be deleted.
Finding all resources known or unknown in all regions and deleting them.
Steps:
Step1: Setting Up the Lab Environment (Optional)
If you have an AWS account with some resources which you don’t need then you can try this on same account or you must create a new AWS account for testing AWS Nuke.
Important Note: AWS Nuke is a destructive tool, so use it with caution even in a non-production environment.
Step 2: Install AWS CLI
If you running this command from your local machine or non-Amazon Linus EC2 server then you must install AWS CLI.
- Running this command installs AWS CLI on Linux.
curl "<https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip>" -o "awscliv2.zip"
sudo apt install unzip
unzip awscliv2.zip
sudo ./aws/install
For further guidance in setting up CLI and configuring it with credentials follow this link. https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html
You must ensure that using are using credentials of administrator level AWS user or root can be used as well (not preferred).
Step 3: Installing AWS Nuke
- For macOS
brew install aws-nuke
- For Linux machines
# Download and extract
wget -c <https://github.com/rebuy-de/aws-nuke/releases/download/v2.25.0/aws-nuke-v2.25.0-linux-amd64.tar.gz> -O - | tar -xz -C $HOME/bin
#Run
aws-nuke-v2.25.0-linux-amd64
You can find the latest version from release
Step 4: Configuring AWS Nuke basic configuration
AWS Nuke offers various configuration options. Explore the configuration file (~/.aws-nuke/config.yml) to customize behavior.
- This is a minimal configuration
regions: # List of regions to execute
- eu-west-1
- us-east-1
account-blocklist:
- "999999999999" # production
accounts:
"000000000000": {} # aws-nuke-example
Step 5: Adding target and excludes
aws-nuke provides option to target or exclude particular resources from deletion. There are multiple ways to configure this.
- Using target to delete certain resources
---
regions:
- "eu-west-1"
account-blocklist:
- 987654321
resource-types:
# only nuke these three resources
targets:
- S3Object
- S3Bucket
- IAMRole
accounts:
98769876: {}
- Using excludes to delete all but specified resources.
---
regions:
- "eu-west-1"
account-blocklist:
- 987654321
resource-types:
# don't nuke IAM users
excludes:
- IAMUser
accounts:
98769876: {}
Step 6: Using resources filtering
aws-nuke provides option to avoid deleting the current user for example or for resources like S3 Buckets which have a globally shared namespace and might be hard to recreate. Currently the filtering is based on the resource identifier.
- For example we can delete all resources but certain
IAMUserandIAMUserPolicyAttachment
---
regions:
- "eu-west-1"
account-blocklist:
- 1234567890
accounts:
0987654321:
filters:
IAMUser:
- "admin"
IAMUserPolicyAttachment:
- "admin -> AdministratorAccess"
IAMUserAccessKey:
- "admin -> AKSDAFRETERSDF"
- "admin -> AFGDSGRTEWSFEY"
aws-nuke supports using multiple types of filters like exact filter, contains, regex, date based etc.
Example configuration file.
version: 0.34.0 # Replace with the installed version
resources:
- type: EC2
filters:
- Name: tag:Name=chandra-ec2
- type: S3Bucket
filters:
- Name: name # Matches bucket names containing "test"
values:
- application-data-store-12345364
Explanation of the configuration file
version: Specifies the AWS Nuke version used.resources: This section defines the resources to target.The first entry targets EC2 instances with the tag
Name: My-Test-Instance.The second entry targets S3 buckets containing "test" in their names.
Filters:
Filters allow for more granular targeting within a resource type.
In the first entry, we use a tag filter to target a specific EC2 instance.
The second entry uses a name filter with a value to target buckets containing
application-data-store-12345364.
Step 7: Executing a dry run
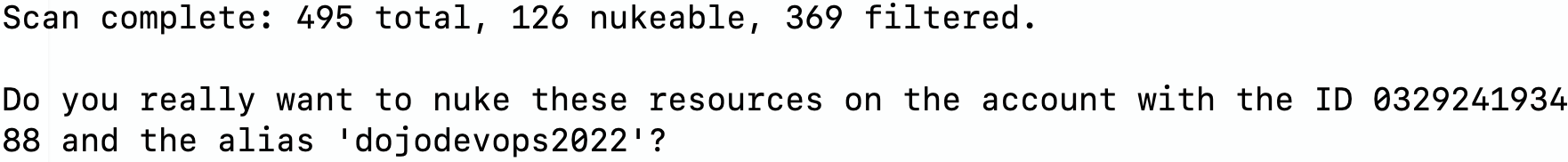
AWS Nuke is very distructive so it provides option to perform a dry run to see which resources would be deleted.
- Run the following command with flag
--dry-runin the config path.
aws-nuke --dry-run -c nuke-config.yml
This command simulates the deletion process based on your configuration. It will display a list of resources slated for deletion without actually deleting them.
Step 8: Review and Deletion (ACTUAL & DISTRUCTIVE)
This step involves actual resource deletion. Here we just remove the --dry-run flag and run only when we are confident in the targeted resources.
Important: This will permanently delete the targeted resources. Use this step with extreme caution!
Result
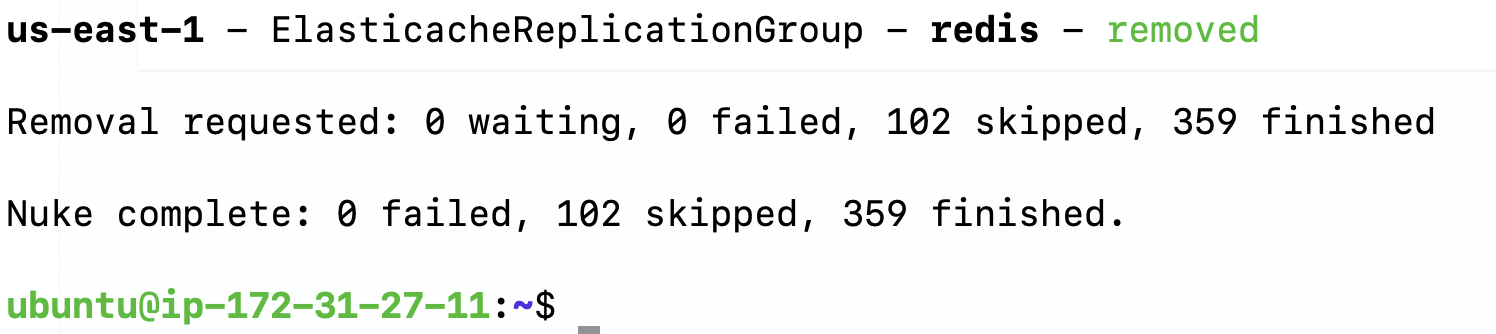
Easily removed AWS resources giving me peace of mind with no surprise bills anymore.